24-HR Cyberattack Summary
Reporting Period: November 23-24, 2025
1. EXECUTIVE SUMMARY
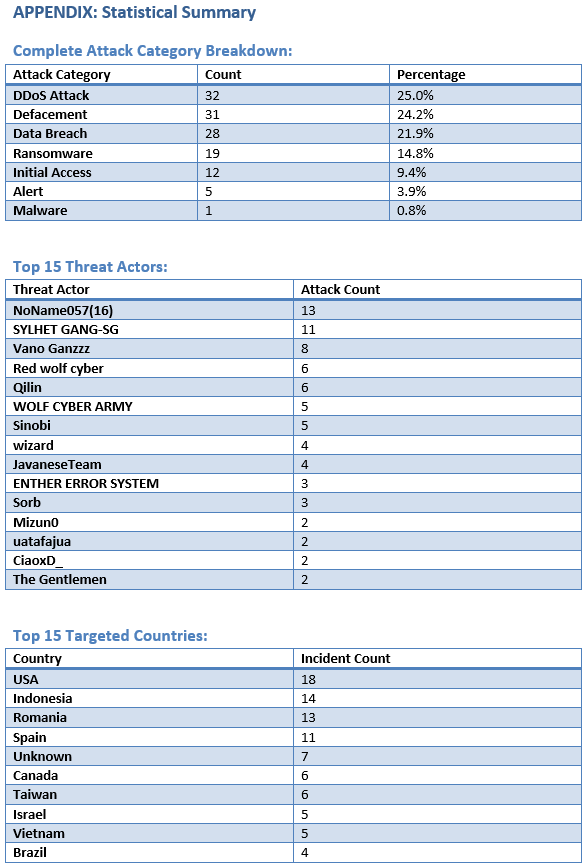
Over the past 24 hours, the global cyber threat landscape witnessed 128 documented security incidents spanning 32 countries and impacting 46 distinct industry sectors. The attack profile reveals a diversified threat environment with 63 unique threat actors actively conducting operations.
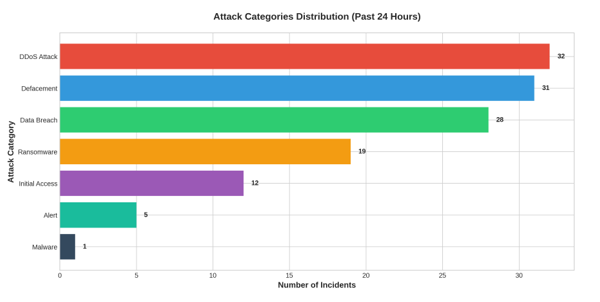
The dominant attack vectors were DDoS attacks (32 incidents, 25.0%), website defacements (31 incidents, 24.2%), and data breaches (28 incidents, 21.9%). Ransomware operations maintained significant activity with 19 confirmed incidents.
The United States emerged as the most targeted nation with 18 incidents, followed by Indonesia (14 incidents) and Romania (13 incidents). Government Administration and Transportation & Logistics sectors faced the highest concentration of attacks, reflecting continued strategic targeting of critical infrastructure.
Key Findings:
· Total Security Incidents: 128
· Most Active Threat Actor: NoName057(16) (13 attacks)
· Primary Attack Type: DDoS Attack (32 incidents)
· Most Targeted Country: USA (18 incidents)
· Most Targeted Industry: Government Administration (16 incidents)
2. KEY STATISTICS & ANALYSIS
2.1 Analysis of Attack Categories
The attack landscape over the past 24 hours demonstrates a concentration in three primary threat vectors:
DDoS (Distributed Denial of Service) attacks dominated the threat landscape with 32 incidents (25.0% of total activity), targeting primarily transportation infrastructure and government services. These coordinated disruption campaigns indicate sophisticated actors with significant botnet resources.
Website defacements accounted for 31 incidents (24.2%), primarily affecting educational institutions and small-to-medium enterprises. This activity suggests opportunistic targeting of vulnerable web applications and content management systems.
Data breach operations comprised 28 incidents (21.9%), with threat actors claiming unauthorized access to sensitive databases, customer records, and personally identifiable information (PII). The commoditization of stolen data continues to drive this attack category.
Ransomware operations maintained a steady presence with 19 confirmed incidents (14.8%), demonstrating the persistent threat of data encryption and extortion campaigns.
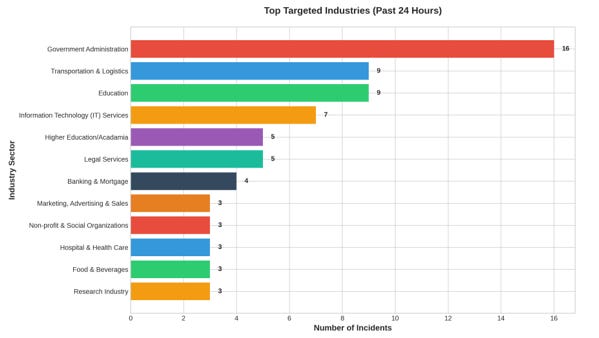
2.2 Analysis of Targeted Victim Industries
The sectoral distribution of attacks reveals strategic targeting patterns across critical infrastructure and high-value industries:
Government Administration emerged as the primary target with 16 incidents, representing sustained adversary interest in disrupting public services and accessing sensitive governmental data. This targeting includes customs services, immigration systems, and municipal infrastructure.
The Transportation & Logistics sector faced 9 incidents, with attacks concentrated on metro systems, aviation authorities, and shipping infrastructure. This targeting pattern suggests both hacktivist motivations and potential reconnaissance for future supply chain disruptions.
Education institutions sustained 9 incidents, reflecting the sector’s continued vulnerability to opportunistic attacks. Educational networks often represent soft targets due to resource constraints and legacy systems.
The Information Technology Services sector experienced 7 incidents, demonstrating the cascading risk when technology providers themselves become compromised.
Financial services (Banking & Mortgage) faced 4 incidents, while Legal Services organizations encountered 5 attacks, indicating targeted operations against high-value data repositories.
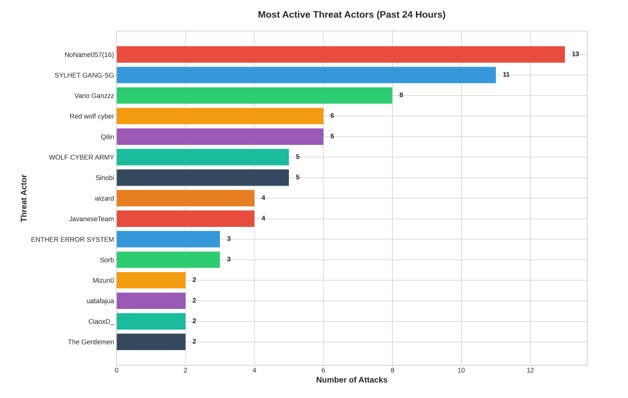
2.3 Analysis of Active Threat Actors
The 24-hour period saw activity from 63 distinct threat actors, ranging from established ransomware groups to hacktivist collectives and opportunistic cybercriminals.
NoName057(16) emerged as the most prolific actor with 13 documented attacks, exclusively conducting DDoS operations against European targets. This pro-Russian hacktivist group maintained its established pattern of targeting critical infrastructure in support of geopolitical objectives.
SYLHET GANG-SG demonstrated significant activity with 11 attacks, focusing on website defacements across multiple countries. This pattern indicates coordination and shared tooling within the group.
Notable ransomware operations were conducted by:
• Qilin ransomware group: 6 incidents targeting North American enterprises
• Sinobi ransomware: 5 incidents with data exfiltration claims
• Additional ransomware families maintained operational tempo with targeted campaigns
The diversity of threat actors indicates a fragmented but highly active threat landscape, with different groups pursuing distinct tactical objectives ranging from financial extortion to ideological disruption.
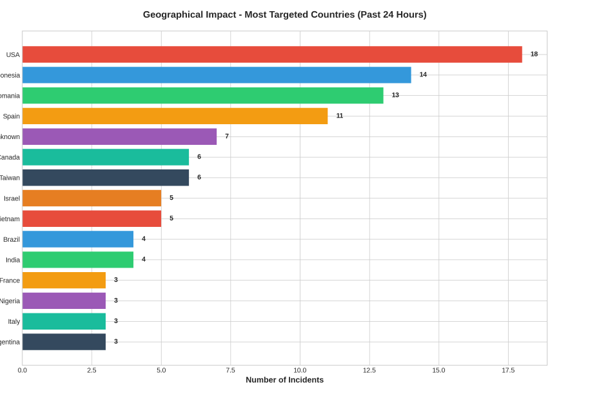
2.4 Analysis of Geographical Impact / Victim Countries
The geographical distribution of attacks reveals concentrated targeting of Western nations, Southeast Asian countries, and Eastern European states:
The United States sustained the highest attack volume with 18 incidents (14.1% of global activity), spanning ransomware operations, data breaches, and defacement campaigns. The diverse attack portfolio suggests both opportunistic and targeted operations against American entities.
Indonesia experienced 14 incidents, primarily consisting of website defacements targeting educational and governmental websites. This activity reflects regional hacktivist operations and potentially nationalist cyber actors.
Romania faced 13 incidents, with a concentration of DDoS attacks against government infrastructure and transportation systems. This pattern aligns with broader Eastern European targeting by pro-Russian cyber actors.
Spain endured 11 incidents, predominantly DDoS operations against transportation infrastructure conducted by NoName057(16). The sustained campaign against Spanish targets represents a coordinated disruption effort.
Additional notable targets included:
• Taiwan: 6 incidents (primarily DDoS against government websites)
• Canada: 6 incidents (mix of ransomware and data breaches)
• Israel: 5 incidents (concentrated DDoS campaigns)
• Vietnam: 5 incidents (data breaches and defacements)
The geographical spread indicates both opportunistic global scanning and deliberate targeting based on geopolitical motivations.
3. DETAILED ANALYSIS & KEY OBSERVATIONS
3.1 Spotlight on Top Threat Actor: NoName057(16)
NoName057(16) represents one of the most active pro-Russian hacktivist collectives currently operating in the cyber domain. Over the 24-hour assessment period, the group conducted 13 documented attacks, exclusively employing DDoS tactics to disrupt target infrastructure.
Tactical Profile:
The group’s modus operandi centers on volumetric DDoS attacks designed to overwhelm target websites and render them inaccessible to legitimate users. All 13 attacks utilized distributed denial of service methodology, indicating access to substantial botnet resources or DDoS-for-hire services.
Targeting Pattern:
NoName057(16) demonstrated strategic targeting of critical infrastructure and public-facing services:
• Transportation & Logistics: 8 incidents (metro systems, transit authorities)
• Government Administration: 3 incidents (customs services, government portals)
• Energy & Utilities: 1 incident
• Hospitality & Tourism: 1 incident
Geographical Focus:
The threat actor maintained concentrated operations against specific nations:
• Spain: 10 attacks (sustained campaign against transportation infrastructure)
• Ukraine: 2 attacks (targeting government services)
• Poland: 1 attack (municipal CCTV systems)
This targeting aligns with the group’s documented pro-Russian geopolitical motivations, focusing disruption efforts on NATO member states and Ukrainian government infrastructure.
Implications:
NoName057(16)’s sustained operational tempo suggests dedicated resources and clear strategic objectives. Organizations in targeted sectors and regions should implement robust DDoS mitigation strategies, including traffic filtering, rate limiting, and engagement with DDoS protection services. The group’s predictable targeting patterns enable proactive defensive posturing.
3.2 Vulnerability Analysis: Government Administration Sector
The Government Administration sector faced 16 incidents over the 24-hour period, representing 12.5% of all documented attacks. This sustained targeting reflects the sector’s high-value data repositories and its critical role in public infrastructure.
Threat Profile:
Government entities encountered a diverse array of attack methodologies:
• DDoS Attacks: 12 incidents (75.0%)
• Initial Access Operations: 2 incidents
• Data Breaches: 1 incidents
• Defacement Campaigns: 1 incident
The prevalence of DDoS operations indicates adversary objectives centered on service disruption and visibility rather than data exfiltration. However, the presence of initial access and data breach operations demonstrates more sophisticated intrusion attempts.
Active Threat Actors:
Multiple threat actors targeted government infrastructure:
• NoName057(16): 3 DDoS attacks (pro-Russian hacktivist collective)
• Red wolf cyber: 3 DDoS operations
• Additional actors conducting opportunistic reconnaissance and access operations
Vulnerability Factors:
Government organizations face unique cybersecurity challenges:
1. Legacy Systems: Aging infrastructure with delayed patching cycles creates exploitable vulnerabilities
2. Public-Facing Services: Citizen-facing portals and services present larger attack surfaces
3. Budget Constraints: Limited cybersecurity funding relative to private sector counterparts
4. Geopolitical Targeting: Nation-state and hacktivist actors specifically target government entities for ideological or strategic reasons
Recommended Mitigations:
• Implement comprehensive DDoS mitigation strategies including traffic scrubbing and rate limiting
• Accelerate vulnerability patching cycles, particularly for internet-facing systems
• Deploy network segmentation to isolate critical systems from public-facing infrastructure
• Enhance monitoring and logging capabilities for early threat detection
• Conduct regular security assessments and penetration testing
• Establish information sharing partnerships with other government entities and ISACs
3.3 Key Trends Observed
Analysis of the 24-hour dataset reveals several significant trends that warrant continued monitoring:
1. Hacktivist DDoS Campaigns Maintain Intensity
DDoS operations accounted for 32 incidents (25.0% of total activity), with concentrated campaigns by pro-Russian groups targeting NATO member states. The sustained operational tempo of groups like NoName057(16) indicates persistent geopolitical cyber operations. This trend is expected to continue as long as geopolitical tensions remain elevated.
2. Educational Sector Vulnerability Exploitation
Educational institutions faced significant targeting, with 9 attacks against Education sectors and 5 attacks against higher education specifically. The continued exploitation of educational networks reflects their attractive profile: valuable data, limited security resources, and expansive attack surfaces. Summer periods and semester transitions may see intensified opportunistic targeting.
3. Ransomware Operations Targeting Healthcare and Professional Services
Ransomware groups conducted 19 operations, with notable targeting of dental practices, healthcare facilities, and professional services firms. Groups like Qilin (6 incidents), Sinobi (5 incidents), and others maintained active operations. The healthcare sector’s criticality and willingness to pay ransoms continues to make it a priority target.
4. Indonesian Web Defacement Surge
Indonesia experienced 14 incidents, predominantly website defacements by groups like SYLHET GANG-SG and JavaneseTeam. This concentrated activity suggests regional hacktivist operations or coordinated campaigns by organized cyber groups operating in Southeast Asia.
5. Data Breach Commoditization
Data breach operations (28 incidents) increasingly featured claims of database sales on underground forums. Threat actors advertised stolen credentials, PII databases, and corporate data, reflecting the mature criminal ecosystem for monetizing stolen information. Notable examples included banking credentials, ID documents, and customer databases.
6. Initial Access Broker Activity
12 initial access incidents were documented, including VPN access sales and leaked credentials. The initial access broker economy continues to enable subsequent ransomware and data exfiltration operations by providing turnkey entry points to target networks.
7. Cross-Sector Critical Infrastructure Targeting
Transportation infrastructure faced sustained attacks (9 incidents), while government services encountered 16 incidents. This pattern indicates strategic targeting of interdependent critical infrastructure sectors, potentially for future coordinated disruption campaigns.
Strategic Implications:
Organizations should anticipate continued diversification of threat actors and attack methodologies. The concentration of DDoS and defacement operations suggests a bifurcated threat landscape: sophisticated ransomware groups conducting targeted operations alongside opportunistic hacktivists pursuing visibility and disruption. Defense strategies must address both threat profiles through layered security controls, threat intelligence integration, and rapid incident response capabilities.

The geographic targeting patterns you've documented here are really interseting. NoName057(16)'s sustained focus on Spanish transportation infrastucture shows how these groups are becoming more strategic rather than just opportunistic. The fact that government adminstration faced 75% DDoS attacks while still seeing initial access operations suggests defenders need to worry about both the noise and what might be happening quietly behind it.